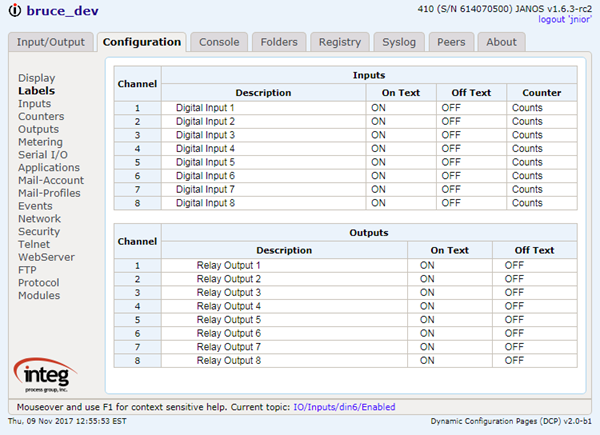
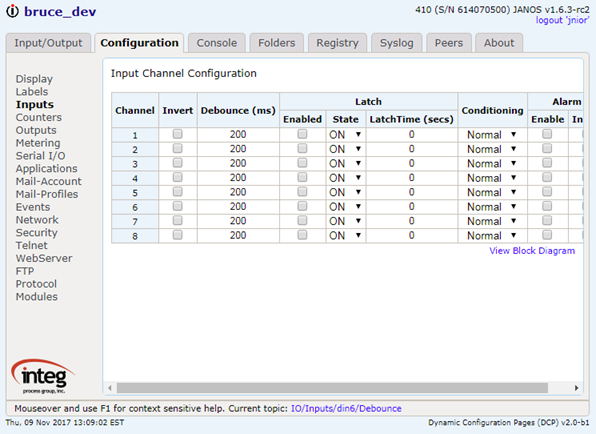
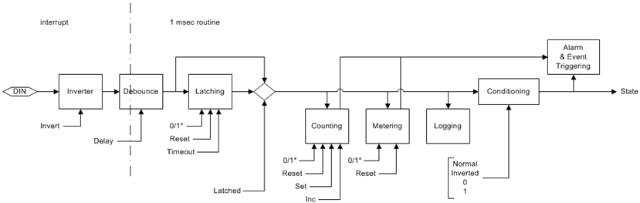
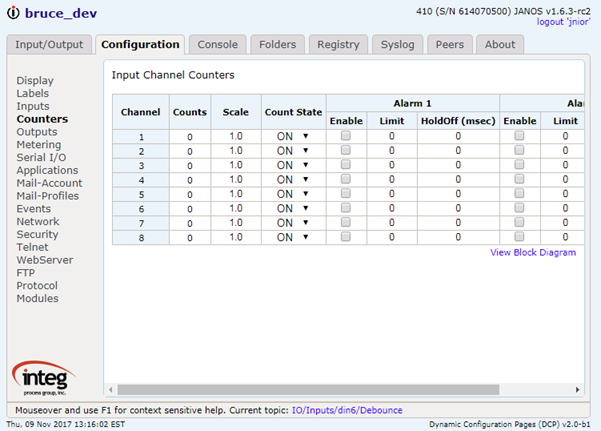
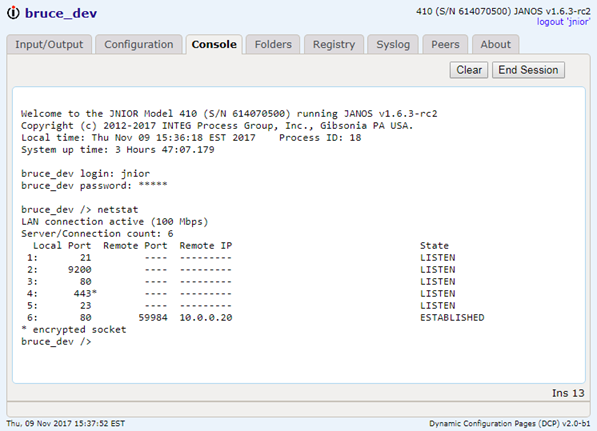
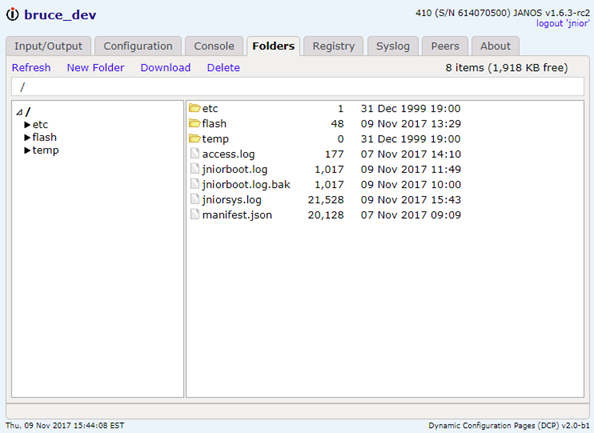
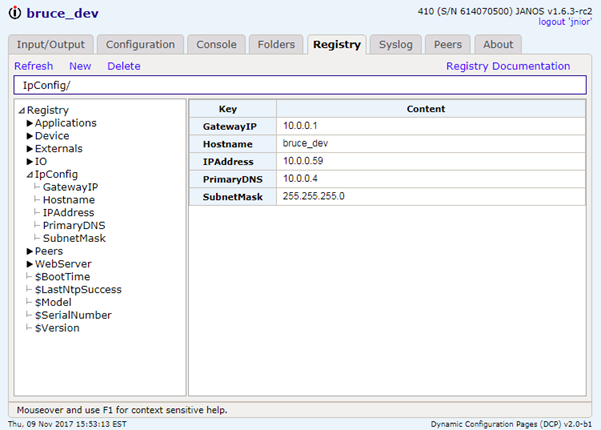
The CAT command outputs the content of a file to the display. It has an alias the TYPE command.
The CAT -P option displays the last 25 lines of a text file. The jniorsys.log file can get quite lengthy as it may contain up to 64KB in characters. Each new event is added to the end of the file (displayed in reverse order in the Syslog tab of the DCP). So if you are interested only in the most recent events, use the -P option to display just the end of the file.
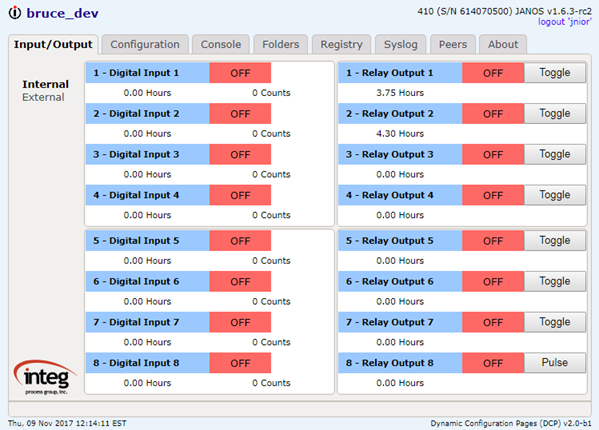
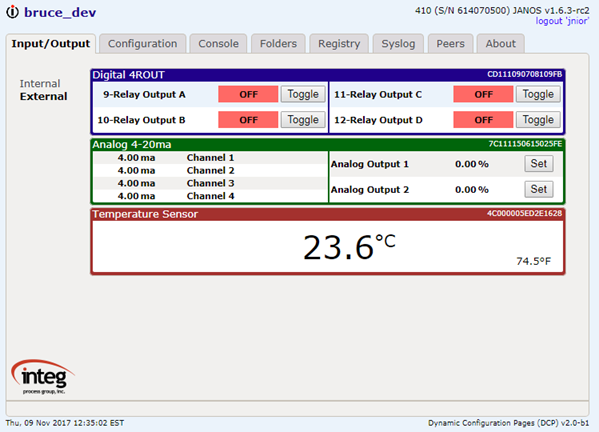
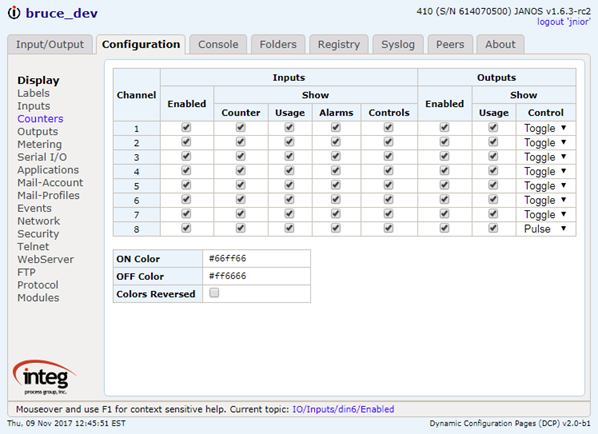
Here’s an example of a text file.
The CAT -H option dumps a file in hexadecimal. I’ll insert it in a CODE box so you can scroll it.
This can be useful at times.
And finally one interesting option. The CAT -J command will format a JSON file. JANOS can work with JSON (http://www.json.org/) and you may create files in that format for configuration or database operations. The MANIFEST command keeps its database in JSON format. I’ll dump it and add it here in a CODE block so you can scroll through it.
CODE: Select All
bruce_dev /> cat -j manifest.json
{
"model":"410",
"serno":614070500,
"vers":"v1.6.3-b3",
"date":"10/26/17 14:07:19",
"files":{
"/etc/janosclasses.jar":{
"length":243492,
"date":1507823966,
"md5":"9b428bdd71054cb88c7e46851dba7307",
"crc":"d81734ca",
"sha":"ca80fd476f2ac6fc2d2b39b65faad72a9570a1ca"
},
"/flash/serialcontrol.jar":{
"length":31344,
"date":1450364184,
"md5":"b349e02b7efc64c0dfe5eb74292a5ee6",
"crc":"3a005104"
},
"/flash/serialethernet.jar":{
"length":25266,
"date":1433505362,
"md5":"ee5e266bb8418b4223a666bd046a8c56",
"crc":"c3961df2"
},
"/flash/modbusserver.jar":{
"length":51907,
"date":1502219129,
"md5":"77c16d6134dbd7ec93313fbad2b00d93",
"crc":"b7456b42",
"sha":"fad4ecc3d1607aafe0a385a10fb5ee90eff521bd"
},
"/flash/snmp.jar":{
"length":239949,
"date":1493062048,
"md5":"b77d35c322ef6645f1eca9d22b29400b",
"crc":"a4073dcb",
"sha":"44a3c2b41a2375ef603063cc9b04642903dad973"
},
"/flash/www/base64.js":{
"length":3493,
"date":1433505378,
"md5":"1138db1b5a6e165beae3ed81739dd2ec",
"crc":"baceb6f6"
},
"/flash/www/configure/index.html":{
"length":1349,
"date":1433505382,
"md5":"0454014aecfd0b7d9e4ce1efe0979139",
"crc":"11ba5486"
},
"/flash/www/jr310applet.jar":{
"length":287159,
"date":1441207703,
"md5":"f9c4840e7244824b75858a1a40dfb163",
"crc":"3d1d0c72"
},
"/flash/www/jniorprotocol.jar":{
"length":115148,
"date":1441207710,
"md5":"404b40c4293bf3c334e3b88e2fe0dd10",
"crc":"5143ec4f"
},
"/flash/www/jniorprotocolhelpers.jar":{
"length":34991,
"date":1433505394,
"md5":"b08e33e0c21e6c075b9b242bf092b68e",
"crc":"48990308"
},
"/flash/www/task/index.html":{
"length":1415,
"date":1433505397,
"md5":"bbdc32dce371881b3eebd15f5b3fce96",
"crc":"cdbe02e4"
},
"/flash/www/taskmanagerinterface.jar":{
"length":123052,
"date":1433505400,
"md5":"077cddccee476fab552d52a5eefd26a7",
"crc":"647bb4b3"
},
"/flash/www/jquery/jquery-1.9.0.min.js":{
"length":93071,
"date":1433505404,
"md5":"2b869ea9c8edd4c2243c5d44f665f632",
"crc":"6a2a8434"
},
"/flash/www/jquery/jquery-ui.css":{
"length":33441,
"date":1433505405,
"md5":"c6bd2971b8e625f2ae43ede9f655a27b",
"crc":"0497b7a6"
},
"/flash/www/jquery/jquery-ui.min.js":{
"length":96395,
"date":1433505409,
"md5":"8f636d4c90ea0abfcbb25528c635bf7d",
"crc":"820662f5"
},
"/flash/www/vendor/bowser/bowser_0.7.2.min.js":{
"length":3359,
"date":1433505412,
"md5":"61a36d48aad1298b17284b53f6ce3fd1",
"crc":"22deb9e6"
},
"/flash/www/text":{
"length":1336,
"date":1434044220,
"md5":"bab65804218b18b9e1a79f2d8e873259",
"crc":"dda17d61"
},
"/flash/www/cycle":{
"length":419,
"date":1434044214,
"md5":"9eb9bbdae70c1f994ebb7f51b18783b8",
"crc":"9e496eb9"
},
"/flash/slaveservice.jar":{
"length":73323,
"date":1465435094,
"md5":"cd6f5e177d75675607e9523d52e133f7",
"crc":"9a871cd7"
},
"/flash/ftp.jar":{
"length":9563,
"date":1475783634,
"md5":"793e460054f07867685e87f98fd402e6",
"crc":"36fd641e"
},
"/flash/task.ini":{
"length":4311,
"date":1433782061,
"md5":"b1f877ac198306b266311eab557ed1dd",
"crc":"36a57579"
},
"/flash/task.jar":{
"length":102655,
"date":1434645611,
"md5":"1979b16970127f2c38912777cb105133",
"crc":"ed4d6ad7"
},
"/flash/jnior.ini":{
"length":4874,
"date":1509041097,
"md5":"7d723f1d36f2f743d2cb6b9b3ba456a6",
"crc":"ae5d2732",
"sha":"e798e12e57bedaacb9bdfd9ef11c2ad863e6691e"
},
"/jniorsys.log":{
"length":32844,
"date":1509041111,
"md5":"6fa593ed95db856d0825bae724dce983",
"crc":"d4d89669",
"sha":"8ba4e9a6563b0a5dc2c0c5726446427d648ac727"
},
"/jniorboot.log.bak":{
"length":1041,
"date":946684814,
"md5":"dfe9684a2933723a8cb54c30e4ee910e",
"crc":"b0dcd002",
"sha":"5f32c14164cf2ae3570ac0e06ec486c70ffe77e6"
},
"/jniorboot.log":{
"length":995,
"date":1509041097,
"md5":"1a3f2d4e7d92774c72b4b1a05465a09b",
"crc":"c5855a0b",
"sha":"29ca5cf807094c8212d7fd467fd506e043c2582c"
},
"/flash/benchmark.jar":{
"length":24351,
"date":1464873509,
"md5":"987f4044786771f31e0656cf91ed73f3",
"crc":"1eed095a"
},
"/flash/threadtest.jar":{
"length":3601,
"date":1434645124,
"md5":"902ce61cbd2524ca9b83dea335c395d3",
"crc":"cd2479ff"
},
"/flash/test4to20.jar":{
"length":3862,
"date":1434659455,
"md5":"a2e309c9d6dd112e5303aa76d2470740",
"crc":"976f8208"
},
"/flash/dirs.bat":{
"length":87,
"date":1435691869,
"md5":"531d655733ee668d829f9b3bdad96038",
"crc":"6a11f77a"
},
"/flash/www/console/index.php":{
"length":4347,
"date":1438974987,
"md5":"8728680bbc36d369429f7ca2c73cce7d",
"crc":"c939c423"
},
"/flash/clean.bat":{
"length":56,
"date":1436532855,
"md5":"ac9ce6553e1629412fb426b342440493",
"crc":"3b661614"
},
"/flash/jnior1024.key":{
"length":887,
"date":1437746752,
"md5":"b76b5351a92fdcc8d9b6b38ca62d8d71",
"crc":"7983e14c"
},
"/flash/www/config/md5.js":{
"length":5693,
"date":1433505379,
"md5":"a60fec5a81f207ff99ec1b97e3ccad0e",
"crc":"e2a43d16"
},
"/flash/www/config/node.png":{
"length":253,
"date":1440435886,
"md5":"1a8dbfaf1771a06e48dea0e3dc604392",
"crc":"799c6dfc"
},
"/flash/www/config/tabs-styles.css":{
"length":970,
"date":1477590404,
"md5":"68bca7015f51e26ab42199b5eb17a356",
"crc":"f8870a33"
},
"/flash/www/config/tabs.js":{
"length":3662,
"date":1449678641,
"md5":"ff728c86018341548ee70028062c89e0",
"crc":"1a813112"
},
"/flash/www/config/styles.css":{
"length":4450,
"date":1504814044,
"md5":"9ad78cca1b794dbcf9db3c55f1be5f1b",
"crc":"acbd2e14",
"sha":"3cf0bbc864840994a49f62d0ae00df6d8eb47ef3"
},
"/flash/www/config/comm.js":{
"length":3541,
"date":1507912287,
"md5":"e7d2e56a443176d6150bbcc8b56e1911",
"crc":"0ac0ed26",
"sha":"5e66b96227779c5ef3736a7ca891a43cacffbbf1"
},
"/flash/www/config/console.js":{
"length":5137,
"date":1504815652,
"md5":"33289e4b09f462efdb50e8d30d22d791",
"crc":"b89fe380",
"sha":"c2f3ea4fc0344d43b0c30b7f60b2b6c79c1f4817"
},
"/flash/www/config/config.js":{
"length":12639,
"date":1507912576,
"md5":"75bf22a88d8a23b17de267607b88a14c",
"crc":"d693e2f4",
"sha":"cf9e9bcf7cc7d79ae648b241af16ee194199d7b3"
},
"/flash/www/config/index.php":{
"length":22103,
"date":1508861011,
"md5":"12541c75de413fa0a33fc83313a1302e",
"crc":"9c9d30a2",
"sha":"f1f264aa446f2e02f106f56c87997ed305b335a7"
},
"/flash/www/jnior.ico":{
"length":3262,
"date":1439548680,
"md5":"1c3b3dda6b10c6259fcf7c068b760f09",
"crc":"051803eb"
},
"/flash/www/favicon.ico":{
"length":156790,
"date":1486410493,
"md5":"07cb90c7f3573eff80222269625ed1dd",
"crc":"7e367afa",
"sha":"284add71fe3d3ba48fba059b88ff5143d3964b1d"
},
"/flash/analogpresets.jar":{
"length":163902,
"date":1441372806,
"md5":"25eacc647412535e320302d3680ce327",
"crc":"e6b656fc"
},
"/flash/www/config/config.css.php":{
"length":1045,
"date":1475072901,
"md5":"1692861e9abd7f8d81f5b7cf8a176046",
"crc":"4c386a21"
},
"/flash/www/config/inputs.png":{
"length":18047,
"date":1443116143,
"md5":"e2151c93b6cdeaa154d15fab486ae61b",
"crc":"16290877"
},
"/flash/www/config/loading.gif":{
"length":3236,
"date":1264096270,
"md5":"d96f6517e00399c37a9765e045eaaf22",
"crc":"16f442ed"
},
"/flash/jtest.jar":{
"length":1832,
"date":1508935076,
"md5":"acbcb808b9db8e4ffc5a3d7ab873c411",
"crc":"a2062204",
"sha":"d6adbbebc98f9922fe73e5f23c98ff892045377e"
},
"/flash/www/vendor/angular_1.3.15/angular.min.js":{
"length":125909,
"date":1449498838,
"md5":"ca1a58818682c3e858a585f283ab9beb",
"crc":"9d8147d7"
},
"/flash/www/vendor/bootstrap_3.3.0/css/bootstrap-theme.css":{
"length":21740,
"date":1449498835,
"md5":"c64043a3388612233d7eb947918a9bfc",
"crc":"638f58a3"
},
"/flash/www/vendor/bootstrap_3.3.0/css/bootstrap-theme.css.map":{
"length":41933,
"date":1449498838,
"md5":"c5da8241305bfe7e19919e6e943739eb",
"crc":"11260772"
},
"/flash/www/vendor/bootstrap_3.3.0/css/bootstrap-theme.min.css":{
"length":19199,
"date":1449498840,
"md5":"374df0ad5809a5314b0577802430a272",
"crc":"8b3c47b7"
},
"/flash/www/vendor/bootstrap_3.3.0/css/bootstrap.css":{
"length":137590,
"date":1449498845,
"md5":"ad6381ebfa541b55b0152349c6cabf76",
"crc":"371e67da"
},
"/flash/www/vendor/bootstrap_3.3.0/css/bootstrap.css.map":{
"length":366866,
"date":1449498854,
"md5":"4ba278e0c420d166e5a0eb71545f9509",
"crc":"b7c9868d"
},
"/flash/www/vendor/bootstrap_3.3.0/css/bootstrap.min.css":{
"length":114011,
"date":1449498852,
"md5":"78e7f91c0c4cca415e0683626aa23925",
"crc":"34387388"
},
"/flash/www/vendor/bootstrap_3.3.0/fonts/glyphicons-halflings-regular.eot":{
"length":20335,
"date":1449498855,
"md5":"7ad17c6085dee9a33787bac28fb23d46",
"crc":"f171b590"
},
"/flash/www/vendor/bootstrap_3.3.0/fonts/glyphicons-halflings-regular.svg":{
"length":62926,
"date":1449498857,
"md5":"ff423a4251cf2986555523dfe315c42b",
"crc":"385cd4ad"
},
"/flash/www/vendor/bootstrap_3.3.0/fonts/glyphicons-halflings-regular.ttf":{
"length":41280,
"date":1449498858,
"md5":"e49d52e74b7689a0727def99da31f3eb",
"crc":"0617f1ff"
},
"/flash/www/vendor/bootstrap_3.3.0/fonts/glyphicons-halflings-regular.woff":{
"length":23320,
"date":1449498858,
"md5":"68ed1dac06bf0409c18ae7bc62889170",
"crc":"cec1a35c"
},
"/flash/www/vendor/bootstrap_3.3.0/js/bootstrap.min.js":{
"length":34653,
"date":1449498862,
"md5":"281cd50dd9f58c5550620fc148a7bc39",
"crc":"32d6c689"
},
"/flash/www/vendor/bootstrap_3.3.0/js/bootstrap.js":{
"length":65813,
"date":1449498862,
"md5":"d5a03d9cca57637f008124916b86b585",
"crc":"f504a7b3"
},
"/flash/www/vendor/bootstrap_3.3.0/js/npm.js":{
"length":484,
"date":1449498863,
"md5":"ccb7f3909e30b1eb8f65a24393c6e12b",
"crc":"cc50e34d"
},
"/flash/www/vendor/jquery_1.11.1/jquery-1.11.1.min.map":{
"length":141680,
"date":1449498870,
"md5":"ffbeb16578d8cdf58104889baacbbef2",
"crc":"e4e92bfd"
},
"/flash/www/vendor/jquery_1.11.1/jquery-1.11.1.min.js":{
"length":95786,
"date":1449498869,
"md5":"8101d596b2b8fa35fe3a634ea342d7c3",
"crc":"804ff984"
},
"/flash/www/config/integlogo.png":{
"length":5773,
"date":1449163436,
"md5":"9111308273dadea73f5d09a5e02c7311",
"crc":"60c4e184"
},
"/flash/utility.jar":{
"length":106794,
"date":1449773066,
"md5":"ac559b91b537dfa70720a416f32f2960",
"crc":"888936f1"
},
"/flash/generators/json/colour.js":{
"length":4327,
"date":1449774238,
"md5":"c67e10d0e0e698fcdbbbadcaa55600d4",
"crc":"19e8a38f"
},
"/flash/generators/json/ethernet.js":{
"length":1409,
"date":1449774238,
"md5":"1b6bae08feb93f6bd345a3780c3acb69",
"crc":"848097a7"
},
"/flash/generators/json/inputs.js":{
"length":2825,
"date":1449774239,
"md5":"6959db5a769ff3ceea45bf606bda940a",
"crc":"c544d780"
},
"/flash/generators/json/lists.js":{
"length":12006,
"date":1449774239,
"md5":"5cc489ac77db7a3369b2ffc30cbd3a86",
"crc":"ba761254"
},
"/flash/generators/json/logic.js":{
"length":4404,
"date":1449774239,
"md5":"9cd1cf854976ebb69a6c20a7ac88d2f9",
"crc":"6c2189f9"
},
"/flash/generators/json/loops.js":{
"length":6040,
"date":1449774239,
"md5":"e8e9021b5d4eb2e0cc43f11ad5b3bfd7",
"crc":"b30a758a"
},
"/flash/generators/json/math.js":{
"length":14673,
"date":1449774240,
"md5":"fa22c29efc362e02d8f35838fcca46e5",
"crc":"8fc62e67"
},
"/flash/generators/json/other.js":{
"length":983,
"date":1449774240,
"md5":"dd77f555bc9b50ed17a215d7935f10ab",
"crc":"3e07810d"
},
"/flash/generators/json/outputs.js":{
"length":3861,
"date":1449774240,
"md5":"72a118cd7829b5a510e5a901d8863d6e",
"crc":"bdd5e320"
},
"/flash/generators/json/procedures.js":{
"length":3945,
"date":1449774240,
"md5":"cb9fb880bebb3375273353fafc12dc9c",
"crc":"20d43aad"
},
"/flash/generators/json/text.js":{
"length":1363,
"date":1449774241,
"md5":"a0bd39f638202a0800c100b4eac3cbc3",
"crc":"b17b24d6"
},
"/flash/generators/json/timing.js":{
"length":2638,
"date":1449774241,
"md5":"b1ee803dd8e6e00de74e0a3269f0a2ff",
"crc":"489061b8"
},
"/flash/generators/json/variables.js":{
"length":1500,
"date":1449774241,
"md5":"fecce79a400d5e4e1edbe521699fa604",
"crc":"cb724c91"
},
"/flash/generators/json.js":{
"length":4115,
"date":1449774238,
"md5":"cc72f2468eb970110f3f6f0278f43467",
"crc":"25a98f30"
},
"/flash/www/config/link_to.png":{
"length":259,
"date":1450466976,
"md5":"b1ed68183be4f97ce1793139496dbbb4",
"crc":"a067876a"
},
"/flash/www/config/collapsed.png":{
"length":232,
"date":1452087215,
"md5":"ef7dd392142824ec54b7b7188717411c",
"crc":"c7bd8428"
},
"/flash/www/config/linked.png":{
"length":174,
"date":1452088114,
"md5":"56d2755d08a0857ff6e7750c4b2822dd",
"crc":"ff59187e"
},
"/flash/www/config/expanded.png":{
"length":238,
"date":1452097812,
"md5":"905b26e96849524dd6c37e1878f66779",
"crc":"68686921"
},
"/flash/www/config/registry.js":{
"length":8276,
"date":1452271284,
"md5":"fc35855793b2bbfe577e420f34cb0dda",
"crc":"6c73e25a"
},
"/flash/www/config/deletex.png":{
"length":240,
"date":1452284181,
"md5":"2750f1e60d0222d7f3c0752207fb41e7",
"crc":"386b823b"
},
"/flash/www/config/modules.js":{
"length":13520,
"date":1484149578,
"md5":"5d79964a8ca70cc7dc0504c343be3e3c",
"crc":"3c09b9e2",
"sha":"d6f0b3ec60796662acd105694ef39543e3dc50a2"
},
"/flash/www/logging.php":{
"length":4853,
"date":1463582298,
"md5":"170c17bd0962f434eebe699129491912",
"crc":"dce15f4e"
},
"/flash/www/slaving.zip":{
"length":113815,
"date":1465493787,
"md5":"b3e85080154b5a7dc10078a6c6fe75c7",
"crc":"975c987e"
},
"/flash/0-10vtest.jar":{
"length":5053,
"date":1438104444,
"md5":"3a7be82077e29c598bdd8694d47805f4",
"crc":"05e27897"
},
"/flash/4routtest.jar":{
"length":2993,
"date":1373644405,
"md5":"14381605ec8f2f0d0dbe34843b7178b8",
"crc":"8240fc03"
},
"/flash/environ.jar":{
"length":3881,
"date":1476102546,
"md5":"8d738f0145516d287174a00dda32dabc",
"crc":"ff1ecc8b"
},
"/flash/current.key":{
"length":898,
"date":1455116261,
"md5":"035a0d79bd6c8258c12111479fe7353e",
"crc":"cbdd8ffe"
},
"/flash/serialtest.jar":{
"length":4532,
"date":1457448880,
"md5":"48fc4bd9421a5cf275b42235d2f4e2cb",
"crc":"6d86943b"
},
"/flash/intellij.jar":{
"length":969,
"date":1464918560,
"md5":"aea445862e32190fa61abc5d97e5b25f",
"crc":"959a1596"
},
"/flash/jmodule.jar":{
"length":5580,
"date":1465240063,
"md5":"af7d42f427d0e711c4a79c8e1c1d341d",
"crc":"40058988"
},
"/flash/udptest.jar":{
"length":5811,
"date":1465328251,
"md5":"5bbc399b4eb1f5ec427ccbf93c8b135d",
"crc":"3d976325"
},
"/flash/buffer.jar":{
"length":95325,
"date":1467321013,
"md5":"0c66b2a130de483b64b91d87471eb952",
"crc":"5d0819e2"
},
"/flash/display.jar":{
"length":2992,
"date":1468953410,
"md5":"efcfc78470e98842f52579c81c088a2d",
"crc":"5ec67fd0"
},
"/flash/rz.jar":{
"length":13079,
"date":1469638127,
"md5":"c4b7e9f4072d64e3dde9fe5a62406a1e",
"crc":"20367148"
},
"/flash/www/config/folder.png":{
"length":329,
"date":1454662486,
"md5":"316b7810fa502618b4e85788a82617a8",
"crc":"55f20187"
},
"/flash/www/config/file.png":{
"length":286,
"date":1454662486,
"md5":"1b75c23448e9c6eed675404f6130491d",
"crc":"d327c449"
},
"/flash/www/config/warning.png":{
"length":3068,
"date":1332275646,
"md5":"9c96d831cfc50fdedfdc980bc2abb2cf",
"crc":"e90bb05a"
},
"/flash/www/config/folders.js":{
"length":19270,
"date":1504815735,
"md5":"c7a59ef1aea3aad95d3315627d3a3b29",
"crc":"6b1adf25",
"sha":"93d7e851c9a1a65ed45b7c1bbe4368d3d941b32f"
},
"/flash/clktest.jar":{
"length":2616,
"date":1470249535,
"md5":"345b4a9a22ec05bc89bb291b7b047e0e",
"crc":"270f1d8b"
},
"/flash/timesearch.jar":{
"length":4180,
"date":1471371624,
"md5":"bf719e65d8f4be9d7348a621ac69bc2b",
"crc":"25075aa7"
},
"/flash/janosruntime_1.5.1.jar":{
"length":1621696,
"date":1472744987,
"md5":"b8beb71b94b36129534ef4d6ec13f5ab",
"crc":"abc7b327"
},
"/flash/www/config/relays.js":{
"length":4189,
"date":1484587793,
"md5":"803af5c2431b8f58c110260b3f317838",
"crc":"ee9ab3af",
"sha":"21ec766fe220bd0618b43050851f9cd67dd1bf54"
},
"/flash/www/config/temperature.js":{
"length":2870,
"date":1475245816,
"md5":"262c339513007cd746ee01da9a4a843f",
"crc":"d062a444"
},
"/flash/www/config/dimmer.js":{
"length":8255,
"date":1475265861,
"md5":"e7213c6fb8c263ac71acb766e62dc4ce",
"crc":"b9edf051"
},
"/flash/www/config/range.css":{
"length":2212,
"date":1475499110,
"md5":"6932c76ab79879ea4c5d826d9cb60db9",
"crc":"3334dfd1"
},
"/flash/www/config/analog.js":{
"length":7267,
"date":1484587793,
"md5":"87abcaf68dea5e2e203326a55bc2bca5",
"crc":"9766b532",
"sha":"dd788111904d41826164ea151f78dd4b3e3b84e6"
},
"/flash/www/config/ledon.png":{
"length":626,
"date":1475506220,
"md5":"6018d69896fcba49da54c39d8ee19803",
"crc":"32a65f15"
},
"/flash/www/config/panel.js":{
"length":2038,
"date":1475509052,
"md5":"e0631cb06777f63f0a071f7aa5d198d0",
"crc":"a38a7db3"
},
"/flash/www/config/ledoff.png":{
"length":757,
"date":1475509575,
"md5":"4bb71e412a20ae6f098a29b195b10e13",
"crc":"3fd16f7a"
},
"/flash/jpanel.jar":{
"length":3142,
"date":1358430294,
"md5":"39825ccddf7b61c1ad41d261d84f4950",
"crc":"446bee7f"
},
"/flash/www/config/syslog.js":{
"length":1929,
"date":1496773328,
"md5":"4e8ecca50284c2aeae8e8b90db27ded8",
"crc":"ac2a2541",
"sha":"e413d70cc2bb6717448bc84c2980abc764bc3dd6"
},
"/flash/www/config/peers.js":{
"length":5885,
"date":1505835290,
"md5":"2536fc521f916341b98183f6ce0b2453",
"crc":"f2a44392",
"sha":"5d949b8daa8e5081f19c88e42af968b24955e02c"
},
"/flash/www/index.php":{
"length":356,
"date":1477657721,
"md5":"3ba20cf61f44f9ace09104261acf2711",
"crc":"7f8eaed3"
},
"/flash/www/www.zip":{
"length":85751,
"date":1477663620,
"md5":"296baa71d70bf40c1ad6ee0c71066c49",
"crc":"69922bd1"
},
"/flash/www/download1.php":{
"length":465,
"date":1480616431,
"md5":"1f69c84031dbdbe9aeecd634c0ab9607",
"sha":"9770a8f6534f17f86eeb332309b7cbe07441022e",
"crc":"c7b59619"
},
"/flash/www/short.php":{
"length":273,
"date":1481120537,
"md5":"2fb318c42bd07c0ec34551502bc20c73",
"sha":"9b9831ca6abda2a14a922e058430fe114b8b34e0",
"crc":"fbca8ae2"
},
"/flash/peerbot.jar":{
"length":2488,
"date":1482355836,
"md5":"b09d3118cefb7e9b3db6a16fc68954a3",
"sha":"b4cacde3347d8c4e2b4dd464aef26da441db4eaf",
"crc":"7973e5cf"
},
"/flash/ctrlc.jar":{
"length":1510,
"date":1482421756,
"md5":"b7ce2da5b761674e626ae62c4b9edbcc",
"sha":"51a17a3f092333a0a48aa8e6dcebe0ce99cef3de",
"crc":"bd2a0810"
},
"/flash/www.zip":{
"length":87642,
"date":1505216713,
"md5":"0d0cc1e611d77f48a9e7a48a5c5007b5",
"sha":"27371cf36e32d70e2460510d233737a5f01a4ed1",
"crc":"bebf23bf"
},
"/flash/www/config/favicon.ico":{
"length":766,
"date":1486410493,
"md5":"07cb90c7f3573eff80222269625ed1dd",
"sha":"284add71fe3d3ba48fba059b88ff5143d3964b1d",
"crc":"7e367afa"
},
"/flash/www/map.html":{
"length":1170,
"date":1485380108,
"md5":"901c9971c3c591b3d736cd91516960de",
"sha":"5ded94156ca71884af1afae0fcaf1e78d3bac23d",
"crc":"71f8c837"
},
"/flash/jmanifest.jar":{
"length":5651,
"date":1485192866,
"md5":"dfb84226c647a42295d9f671cfb99fa5",
"sha":"a7331cca377c1f96e400ddd5044c01a175ee230f",
"crc":"1a64c6d6"
},
"/flash/jping.jar":{
"length":2174,
"date":1485201152,
"md5":"0d533008847888e0dfcf497c0cff1a96",
"sha":"75fbff5a973b8dac3408fdda46e47e708b585e58",
"crc":"f1203f43"
},
"/flash/jaccess.jar":{
"length":4820,
"date":1485805203,
"md5":"29ce866873686dd133a724e4db29c690",
"sha":"239bf75c1597a25fdbbbb78798fe72971ca15f63",
"crc":"e5ae0d1c"
},
"/flash/somepath/path2/testx.php":{
"length":5282,
"date":1486397961,
"md5":"ce1a071b258c936c65679d6bb67db198",
"sha":"30342828ebaeb69cd8ecefd75f2dd01e80c6388b",
"crc":"ecd9251a"
},
"/flash/bruce_dev.cer":{
"length":902,
"date":1487172768,
"md5":"e9917f27384ddee36817c04c8cde9199",
"sha":"4b2b82a042a0019679c1b071956278f6ddd1f27b",
"crc":"115ed2ae"
},
"/flash/www/config/registrydoc.css":{
"length":21460,
"date":1504201641,
"md5":"15423ca727b03e6b1581910c6ca2eab5",
"sha":"f521b53a4518e7490768d2a8ae0e707c1dfb943b",
"crc":"0d5fd8c9"
},
"/flash/www/config/registrydoc.html":{
"length":169108,
"date":1508861014,
"md5":"c34c31da746778b07448512e982af5b0",
"sha":"f10f92e1a065faacbb557208fa1e4578dfde64e6",
"crc":"c6979f37"
},
"/flash/www/panel/comm.js":{
"length":4715,
"date":1498074333,
"md5":"44aa80868230fbfeee0a3c48c390896d",
"sha":"37b479f65e7e8221d6fd9349439a8193cc645ba7",
"crc":"0d5e92bd"
},
"/flash/www/panel/index.php":{
"length":2648,
"date":1501526934,
"md5":"923ce6739971521191f9000662f38323",
"sha":"a35d1d5f24da487be376595b46598e162e0f5310",
"crc":"ffd86d7b"
},
"/flash/www/panel/panel.js":{
"length":993,
"date":1501527049,
"md5":"9d9a2cbb435ffe8af5bd9d8c0598dccd",
"sha":"2ef881dc8d90b4b0fb80a59d717c7125ca23fb04",
"crc":"4fcd0f37"
},
"/flash/www/panel/panel.css":{
"length":2586,
"date":1501527291,
"md5":"2a3a66d14d7bc6d4b01dfbd745205c7d",
"sha":"886770297a07a594b88430d5db4ae9e23738d118",
"crc":"2dd8a81d"
},
"/flash/www/graphr.zip":{
"length":556637,
"date":1506536442,
"md5":"891b1dfa8d774b85aefcbd8791abe11f",
"sha":"e5d204333658bd5c2f7c5b5ff682911124a10766",
"crc":"62d153fb"
},
"/flash/public/dcp.zip":{
"length":181914,
"date":1504795829,
"md5":"655e8587293f35f11c5c24fc38201d2f",
"sha":"5fcfd8e38826e648f98f8d50f3613deb0d6312b6",
"crc":"da99b7d0"
},
"/flash/test.txt":{
"length":304,
"date":1495131459,
"md5":"fc9f1f5e67928ccb9be3aeaa66cd9e52",
"sha":"6100d999f484f98ab476408c801dd000e579a62c",
"crc":"765047c5"
},
"/flash/dmx.jar":{
"length":4476,
"date":1500567859,
"md5":"3fd35bbe6bbf53a32aecf273275d1839",
"sha":"4f702a87adb060294b553e6bd212672727d5d25f",
"crc":"e81db9aa"
},
"/flash/juptime.jar":{
"length":3201,
"date":1506713589,
"md5":"d4c2482fae18482727c1b2afabcf94b4",
"sha":"86268b720b99760a4ebdb803db53f3f7fd18fd18",
"crc":"44b0878c"
},
"/flash/jscan.jar":{
"length":2189,
"date":1507141493,
"md5":"a0a42e17f003cedcac9c8e662ada6b36",
"sha":"f1cafb56fdae33b66fff9b20cd2ff2705d96da9e",
"crc":"60f00fe2"
}
}
}
bruce_dev />