Trusted Secure Access
The Series 4 JNIOR supports TLS v1.2 and provides for secure communications through HTTPS port 443. Your unit’s certificate however is not signed by a Trusted Root Authority and you will need to approve access. While that procedure results in secure communications the browser tends to make you think otherwise. But, there is a way to get the coveted Green Secure Logo.
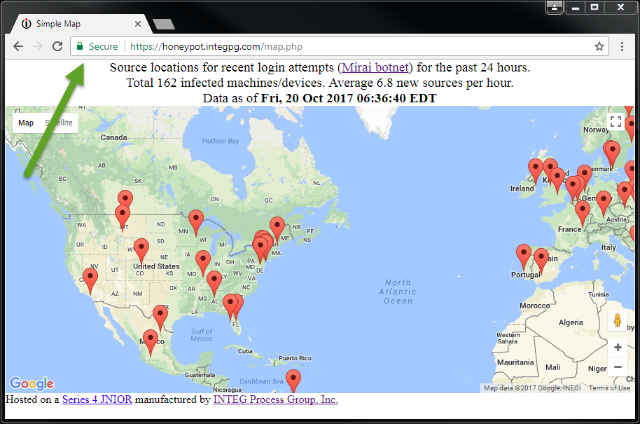
Now when you try to make such a connection you are more than likely going to be confronted by something like this:
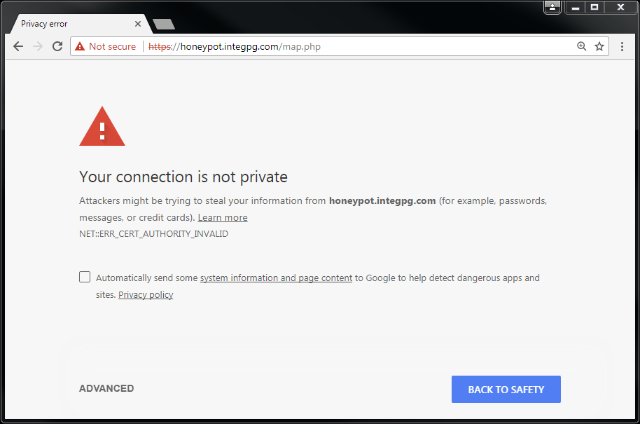
I am using Chrome and every browser has its own way to scare you. In this case I would need to use the ‘ADVANCED’ link in the lower left. In clicking ‘ADVANCED’ there is a bit of an explanation. Here I have to option to proceed.
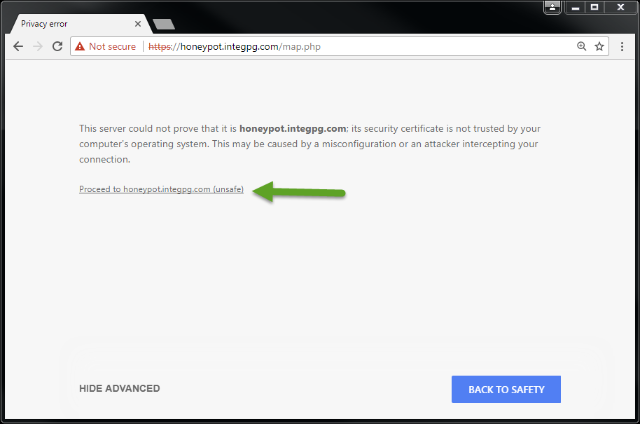
Note that it says “unsafe” but you are accessing the JNIOR and what does the browser know about that? Why is the JNIOR unsafe? But if you were heading to your bank and plan to enter all of your secrets I guess then this might be unsafe. When you proceed (and the JNIOR is safe!) you get the page.
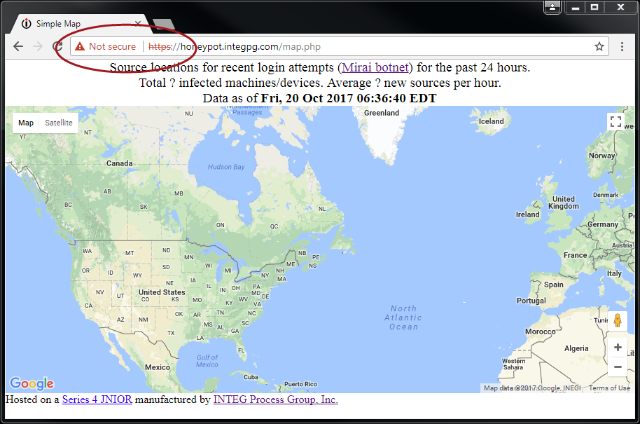
Even though it says that you are “Not Secure” the communications are indeed encrypted and quite secure. The browser just can be certain that you are communicating with someone or something that you can trust. By the way, I snapped the image before the map markers appeared.
Generally you can click on the red “Not Secure” logo and obtain some further details. There generally is some way to view the certificate and potentially trust it. I will show you how that is done at least with my version of Windows 7.
I am going to take you through the manual procedure as a browser-independent approach. First you will need a copy of the JNIOR’s certificate. Now it may be possible to get that using the browser. You would need to do that if you were not the administrator of the JNIOR. That would be the case for you and our HoneyPot unit.
Assuming that you are the administrator of your JNIOR, log into the the command line Console. We are going to use the CERTMGR command to get a copy of the current certificate. Note that when you change the unit’s IP address or hostname a new certificate will be automatically generated That new certificate will be different than one that you may have trusted. So you may need to repeat this for units running DHCP if they are assigned a new IP address and simply don’t continue to renew the same one.
HoneyPot /> help certmgr
CERTMGR
-V Verify installed keys and certificate
-C [file] Regenerate Certificate [Install file]
-S file Verify signature on certificate
-K file Install RSA Key Pair
-D [file] Decode and dump certificate [file]
-E file Export certificate to file
-B Export in binary
-G [len] Generate key pair [bit length]
-R Restore default credentials
SSL Certificate Management.
HoneyPot />So here we see that the -E option will export the certificate. Simply use the following command to export the certificate to a file. The CER extension is appropriate.
Download the honeypot.cer certificate
Finally download this file to your PC. You can do that through the Folders tab in the DCP by double-clicking the file or through FTP however you like.
Now we are going to use the Microsoft Management Console (MMC) to import this certificate into the trusted area. Note that by doing so you are not creating any risk. The JNIOR’s certificate cannot be used to sign other certificates and having it present in the Certificate Store will not trust anything other than your JNIOR (and then only for as long as that certificate stays active).
In the following procedure you will open the MMC as an administrator, add the snap-in that handles Certificates, and import the JNIOR’s certificate into the proper trusted store.
- Open the Start Menu and enter “MMC” to search.
- Right-click on
mmc.exeand select ‘Run as Administrator’. Allow the console to run. - Click ‘File’ and “Add/Remove snap-in..’ from the menu bar.
- From the Available snap-ins select ‘Certificates’ and click ‘Add’. You will be managing certificates for the ‘Computer Account’ on the ‘Local Computer’. Click ‘Finish’ and ‘Ok’ to return to the main MMC screen.
- Expand ‘Certificates (Local Computer)’.
- Expand ‘Trusted Root Certificate Authorities’.
- Click ‘Certificates’. A lengthy list should appear on the right.
- Right-click on ‘Trusted Root Certificate Authorities’ back on the left and select ‘All Tasks’ and ‘Import…’. You can also right-click on ‘Certificates’ over there and get to the same ‘Import..’ action.
- Click ‘Next’ and follow the WIzard. You will browser for your CER file. Then use ‘Next’, ‘Finish’ and ‘Ok’ to perform the import. You should see a message indicating success.
Your certificate will now appear in the lengthy list of root certificates. Note that at some point you may have older certificates here for JNIORs. You can right-click them to ‘Delete; the older ones. Make sure to only delete JNIOR certificates. You don’t want to disturb the computers normal chains of trust.
Now exit the MMC and you don’t need to save the console.
Access your JNIOR using the HTTPS form of URL in your browser and you should now see the Green Secure logo!
Attached is the CER file for HoneyPot as of this writing. This has been pretty stable as this unit has a fixed IP address. If you add this to your Trusted Root Certificate Authorities store you will get the Green Secure logo too.
By the way the JNIOR can show you the content of these CER files. It is pretty cryptic and some of us know what it all means.
HoneyPot /> certmgr -d honeypot.cer
0000 30 82 02 ED SEQUENCE { (749 bytes)
0004 30 82 02 56 | SEQUENCE { (598 bytes)
0008 A0 03 | | [0] EXPLICIT { (3 bytes)
000A 02 01 | | | INTEGER 02
| | }
000D 02 04 | | INTEGER 2499A900
0013 30 0D | | SEQUENCE { (13 bytes)
0015 06 09 | | | OBJECT IDENTIFIER 1.2.840.113549.1.1.11
0020 05 00 | | | NULL
| | }
0022 30 81 81 | | SEQUENCE { (129 bytes)
0025 31 20 | | | SET { (32 bytes)
0027 30 1E | | | | SEQUENCE { (30 bytes)
0029 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.10
002E 0C 17 | | | | | UTF8STRING 'INTEG Process Group Inc'
| | | | }
| | | }
0047 31 17 | | | SET { (23 bytes)
0049 30 15 | | | | SEQUENCE { (21 bytes)
004B 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.11
0050 0C 0E | | | | | UTF8STRING 'JNIOR Controls'
| | | | }
| | | }
0060 31 1D | | | SET { (29 bytes)
0062 30 1B | | | | SEQUENCE { (27 bytes)
0064 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.3
0069 0C 14 | | | | | UTF8STRING 'honeypot.integpg.com'
| | | | }
| | | }
007F 31 25 | | | SET { (37 bytes)
0081 30 23 | | | | SEQUENCE { (35 bytes)
0083 06 09 | | | | | OBJECT IDENTIFIER 1.2.840.113549.1.9.1
008E 16 16 | | | | | IA5STRING 'bcloutier2@comcast.net'
| | | | }
| | | }
| | }
00A6 30 1E | | SEQUENCE { (30 bytes)
00A8 17 0D | | | UTCTIME[13] 170322173023Z
00B7 17 0D | | | UTCTIME[13] 190322173023Z
| | }
00C6 30 81 81 | | SEQUENCE { (129 bytes)
00C9 31 20 | | | SET { (32 bytes)
00CB 30 1E | | | | SEQUENCE { (30 bytes)
00CD 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.10
00D2 0C 17 | | | | | UTF8STRING 'INTEG Process Group Inc'
| | | | }
| | | }
00EB 31 17 | | | SET { (23 bytes)
00ED 30 15 | | | | SEQUENCE { (21 bytes)
00EF 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.11
00F4 0C 0E | | | | | UTF8STRING 'JNIOR Controls'
| | | | }
| | | }
0104 31 1D | | | SET { (29 bytes)
0106 30 1B | | | | SEQUENCE { (27 bytes)
0108 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.3
010D 0C 14 | | | | | UTF8STRING 'honeypot.integpg.com'
| | | | }
| | | }
0123 31 25 | | | SET { (37 bytes)
0125 30 23 | | | | SEQUENCE { (35 bytes)
0127 06 09 | | | | | OBJECT IDENTIFIER 1.2.840.113549.1.9.1
0132 16 16 | | | | | IA5STRING 'bcloutier2@comcast.net'
| | | | }
| | | }
| | }
014A 30 81 9F | | SEQUENCE { (159 bytes)
014D 30 0D | | | SEQUENCE { (13 bytes)
014F 06 09 | | | | OBJECT IDENTIFIER 1.2.840.113549.1.1.1
015A 05 00 | | | | NULL
| | | }
015C 03 81 8D | | | BITSTRING[140] Encapsulates {
0000 30 81 89 | | | | SEQUENCE { (137 bytes)
0003 02 81 81 | | | | | INTEGER
| | | | | A99483174B2EBC8578ECEA5BE9F75840703B06EA49D9333D
| | | | | 493D035A8D84DB5AB7E5491D334BAF1B59A3A271E25C4276
| | | | | D410F3B3C90E801E89A162C6A282EC51AB05CF9731561A95
| | | | | 22A0B3039DF72FA25BA1061E6BBB7A1AA6B287A314FDDBB9
| | | | | E1034B45D5E1FFC15A59C40D772D3CDAD6142A707650F11E
| | | | | BCD30CFF75E65E91
0087 02 03 | | | | | INTEGER 010001
| | | | }
| | | }
| | }
01EC A3 70 | | [3] EXPLICIT { (112 bytes)
01EE 30 6E | | | SEQUENCE { (110 bytes)
01F0 30 1D | | | | SEQUENCE { (29 bytes)
01F2 06 03 | | | | | OBJECT IDENTIFIER 2.5.29.14
01F7 04 16 | | | | | OCTETSTRING[22] Encapsulates {
0000 04 14 | | | | | | OCTETSTRING[20]
| | | | | | 29CB0357BCDD26E78AD5E564C1D087B0 )..W..&....d....
| | | | | | 3B583082 ;X0.
| | | | | }
| | | | }
020F 30 0C | | | | SEQUENCE { (12 bytes)
0211 06 03 | | | | | OBJECT IDENTIFIER 2.5.29.19
0216 04 05 | | | | | OCTETSTRING[5] Encapsulates {
0000 30 03 | | | | | | SEQUENCE { (3 bytes)
0002 01 01 | | | | | | | BOOLEAN TRUE(255)
| | | | | | }
| | | | | }
| | | | }
021D 30 3F | | | | SEQUENCE { (63 bytes)
021F 06 03 | | | | | OBJECT IDENTIFIER 2.5.29.17
0224 04 38 | | | | | OCTETSTRING[56] Encapsulates {
0000 30 36 | | | | | | SEQUENCE { (54 bytes)
0002 87 04 | | | | | | | [7] 32C5224B 2."K
0008 82 14 | | | | | | | [2]
| | | | | | | 686F6E6579706F742E696E7465677067 honeypot.integpg
| | | | | | | 2E636F6D .com
001E 82 08 | | | | | | | [2] 686F6E6579706F74 honeypot
0028 82 0E | | | | | | | [2] 686F6E6579706F745F6A6E696F72 honeypot_jnior
| | | | | | }
| | | | | }
| | | | }
| | | }
| | }
| }
025E 30 0D | SEQUENCE { (13 bytes)
0260 06 09 | | OBJECT IDENTIFIER 1.2.840.113549.1.1.11
026B 05 00 | | NULL
| }
026D 03 81 81 | BITSTRING[128] 0 unused bits
| 2B42E05E331AEEB265F4DAC118DF73E7 +B.^3...e.....s.
| F555D72605F6ECAB67D860324A7C5056 .U.&....g.`2J|PV
| 14C5203337A98C2157D85C57A736B82D .. 37..!W.\W.6.-
| DA88475E93A6C9FC2C5983678C8D461A ..G^....,Y.g..F.
| 9CE7F53A2766DBBD26C0B99CE1F4514F ...:'f..&.....QO
| 6BAC3D09C33000BC7E5F6151C0BA175F k.=..0..~_aQ..._
| 29B6E73B8E7FEBAE1099269A9AFD7067 )..;......&...pg
| 17C67CF9C7F17EBB3F8DB2ED4353C2D1 ..|...~.?...CS..
}
HoneyPot />Download the honeypot.cer certificate.
