Outgoing Secure Socket Connection
Written by Bruce Cloutier on Dec 8, 2017 9:49 am
We showed you how to make an Outgoing HTTP Request. If you would like to make a secure connection you need only add a single line of code.
dataSocket.setSecure(true);
Here I will securely connect from my development JNIOR to the external HoneyPot JNIOR. From the example in the other topic I have modified the host and the request to attempt to access the JNIOR.
package jtest;
import com.integpg.system.Debug;
import java.io.DataInputStream;
import java.io.DataOutputStream;
import java.net.Socket;
public class Main {
public static void main(String[] args) throws Exception {
// Location services
String serverHostname = "50.197.34.75";
int port = 443;
// Establish a Socket, get streams, and set a timeout
Socket dataSocket = new Socket(serverHostname, port);
DataOutputStream sockout = new DataOutputStream(dataSocket.getOutputStream());
DataInputStream sockin = new DataInputStream(dataSocket.getInputStream());
dataSocket.setSoTimeout(5000);
// Negotiate a secure connection
dataSocket.setSecure(true);
// Issue the HTTP request
sockout.writeBytes("GET / HTTP/1.1\r\n");
sockout.writeBytes("Host: " + serverHostname + "\r\n");
sockout.writeBytes("\r\n");
// Process the response header
int length = 0;
String response;
while ((response = sockin.readLine()) != null) {
// Header ends with blank line
if (response.length() == 0)
break;
System.out.println(response);
if (response.startsWith("Content-Length: "))
length = Integer.parseInt(response.substring(16));
}
System.out.println();
// Obtain the entire response (if any)
response = "";
if (length > 2) {
byte[] resp = new byte[length];
sockin.readFully(resp);
response = new String(resp, "UTF8");
}
// Data (should be JSON)
Debug.dump(response.getBytes());
// Close the Socket
sockout.close();
sockin.close();
dataSocket.close();
}
}bruce_dev /> jtest HTTP/1.1 401 Unauthorized WWW-Authenticate: Digest realm="JANOS Web Server", qop=auth, nonce="66d0bb430469f01e9153358cfa7f" Content-Length: 99 3c 48 54 4d 4c 3e 3c 48-45 41 44 3e 3c 54 49 54 <HTML><H EAD><TIT 4c 45 3e 34 30 31 20 55-6e 61 75 74 68 6f 72 69 LE>401.U nauthori 7a 65 64 3c 2f 54 49 54-4c 45 3e 0d 0a 3c 2f 48 zed</TIT LE>..</H 45 41 44 3e 3c 42 4f 44-59 3e 3c 68 31 3e 34 30 EAD><BOD Y><h1>40 31 20 55 6e 61 75 74 68-6f 72 69 7a 65 64 3c 2f 1.Unauth orized</ 68 31 3e 3c 2f 42 4f 44-59 3e 3c 2f 48 54 4d 4c h1></BOD Y></HTML 3e 0d 0a >.. bruce_dev />
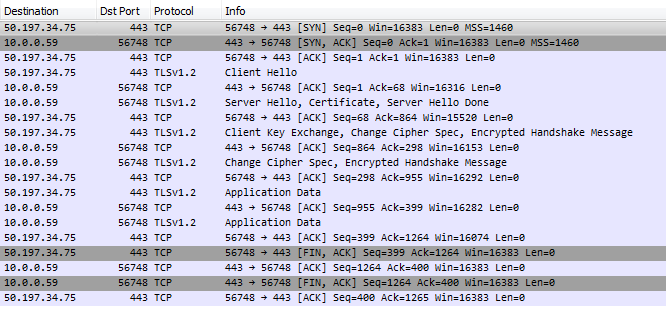
So we get the response expected. But was it done securely? Here’s the transaction from the Wireshark point of view.